Both safety and security in the supply chain can be improved through the use of connected vehicle technology .
However, to be truly effective, in CMS’ view, a best practice method for adoption is this four-step process, which is as much about management as it is about the capabilities of the technology.
The four steps are:
Connection
Collection
Analysis
Action
By adopting these four steps, commercial fleets, insurers, and transport management companies can improve the safety and security in their respective supply chains.
Each of these steps will be explored and detailed below, but first some background information on the technology that supports this, commercial vehicle telematics/connected vehicle technology, and the market challenges that are encountered.
Global market maturity in connected vehicle technology
In terms of competition, breadth of deployment, and use of technology in commercial fleet management, the UK and Italy are regarded as the World’s most highly developed connected vehicle markets.
That is the numbers of suppliers in the market, the level of connection geographically and by devices/capita. The penetration of the telematics technology into fleet management, and the deployment of the latest technology, are all at the highest levels in the UK and Italy.
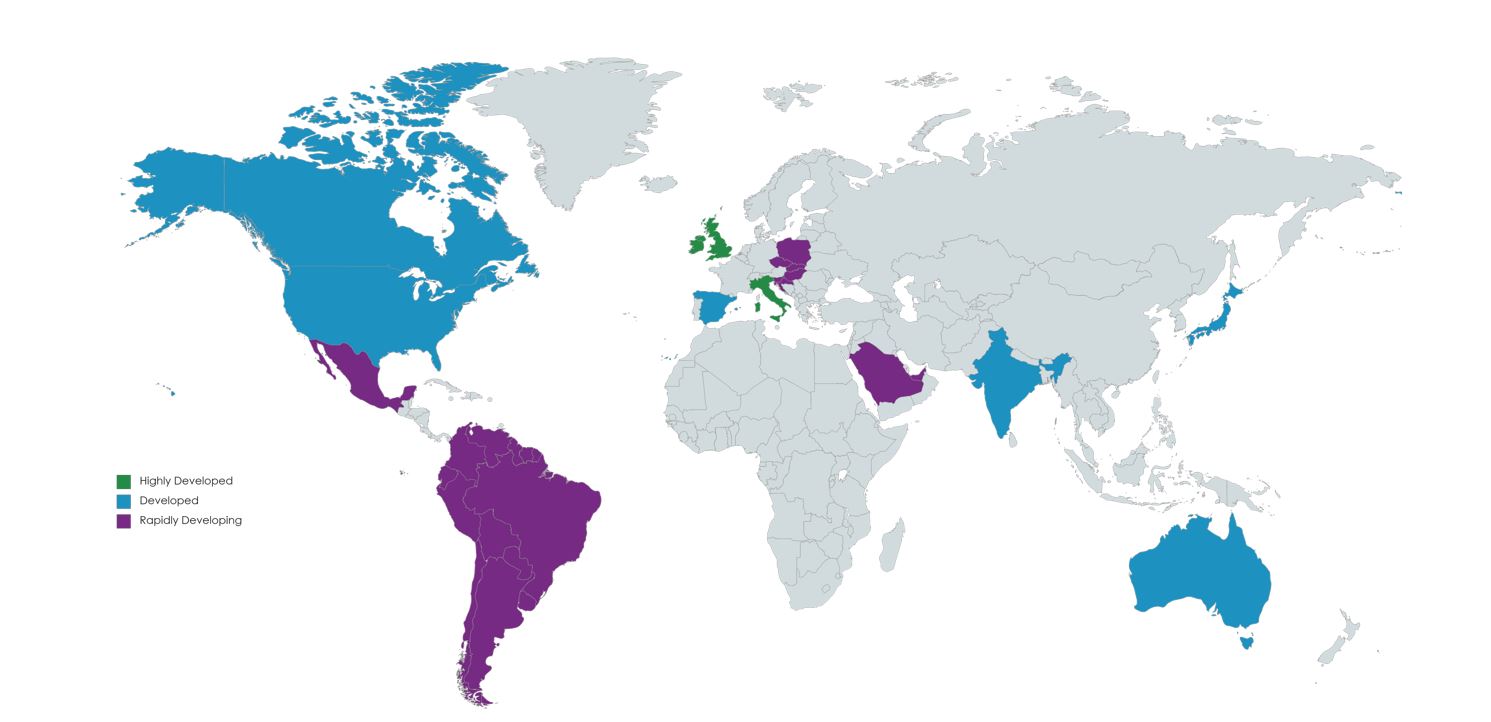
Behind these two countries, North America, Spain, India, Japan, and Australia can all be characterised as being mature and developed telematics markets, but at a level that is behind that of the UK and Italy.
Latin and South America, Central Europe and Saudi Arabia are the regions and countries that fall into the next category. That of a rapidly developing connected telematics markets.
The other parts of the world, while using telematics solutions, have not reached the same level of market competitiveness, business penetration, and/or use of connected telematics. This is down to a myriad of reasons ranging from infrastructure capabilities through to workplace cultures to (lack of) government legislation.
In terms of market size, the global commercial vehicle telematics market has been assessed at £3.6b in 2019, with a 2025 forecast of £4.5b.
The factors driving this growth are increasing safety and security needs, both in the form of corporate responsibility and government regulation. The falling cost of connectivity and the increasing market penetration and integration into connected vehicle systems of smartphones. Plus, a broader appreciation of the benefits of using connected commercial vehicles for cost savings, fleet operational efficiency, improved customer service, and overall business competitiveness.
Five strategic challenges to deploying connected vehicle technology
From CMS’ point of view, based on our working with customers and partners around the world, we see five strategic challenges to the deployment of connected vehicle technology. These have a strong correlation to the maturity of the market.
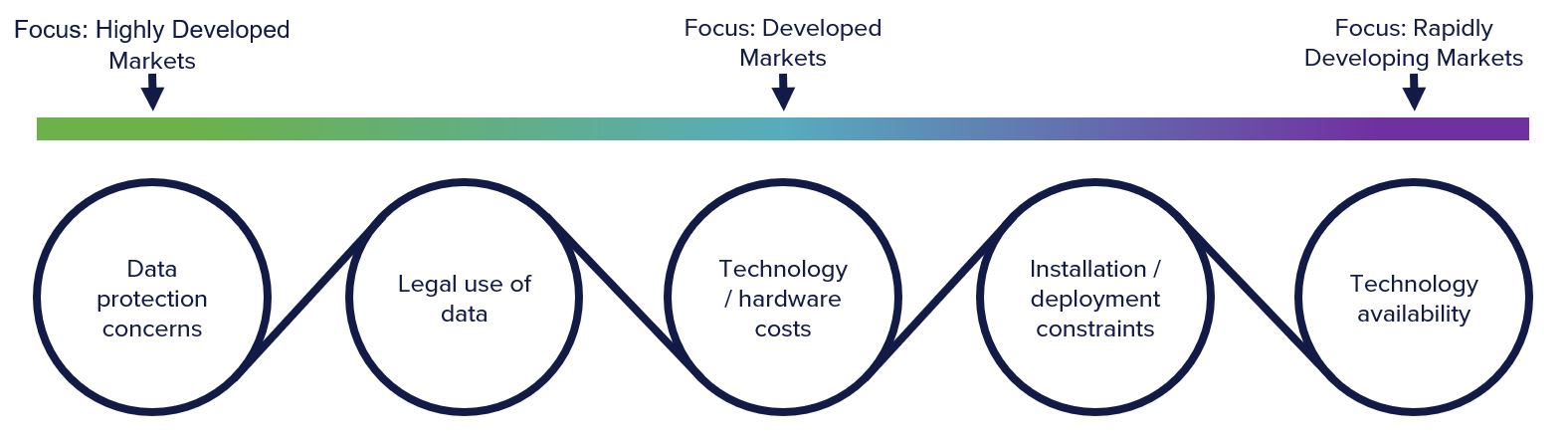
In rapidly developing markets, the availability of the technology and the constraints of installation and deployment are the main challenges.
As markets become more developed, the scaling up of the technologies deployment and the associated costs become the main challenges. As this is overcome, the next challenge, that of the legal use of the data, comes to the fore.
This leads to industry, government and community dialogue about, and legislation around, the lawfulness, fairness, and transparency of the data.
Including the limitations of the purposes it can and can’t be used for. The accuracy requirements and minimal levels of the amount of data that can be collected. The storage security, integrity, confidentiality, and time limits of the data. And ultimately, where the accountability for all these elements sit.
As markets become highly developed, this legal use of the data, rather than the availability installation and deployment of the technology, becomes the main challenge. With all the elements becoming part of a whole, namely that of concerns over data protection.
Here, what data is collected, how, where, what, and why it is used, are defined. The debate and challenge shifts to how that data is protected from its being used by unauthorised third parties.
Of course, there are many additional challenges to do with the tactical deployment and use of connected vehicle technology, such as dealing with the sheer amount of data generated, and these will be highlighted in the sections below.
Step One: Connection.
The first step in using technology to improve safety and security in the supply chain is the connection.
Connected vehicle technology can be grouped into three generations.
Each shows how the type of data that is available and collected by the connection has evolved, meaning that even more insight and management information can be used in security and safety efforts.
Of course, many fleets are at different stages with the hardware they deploy, with a combination of technology generations being common both in and across the categories of hardware.
For example, a fleet could have the majority of its vehicles using 2nd Generation black boxes, but be upgrading to 3rd Generation as it onboards new vehicles, while also staying with a policy of using just two cameras (i.e. 2nd generation) across the whole fleet.
By hardware type the generations are:
Black Box
1st Generation: GPS system to track the vehicle’s location. From this gives speed, route, mileage, drive times etc and is used for route planning efficiency.
2nd Generation: GPS plus events. An evolution of the basic GPS system, which now records events such as harsh breaking, and rapid acceleration, giving an insight into the driver’s behaviour.
3rd Generation: GPS, events, plus diagnostics. Records as per 2nd generation but now integrates vehicle diagnostics and reporting, plus elements such as door opening and closing, engine load and idle times, and the use of seatbelts.
Cameras
1st Generation: SD Card based, and as such, not connected. Require a manual process of taking the cards out of the camera and vehicle and passing onto the fleet management team. Useful in dispute resolution and related insurance claims, but not a real time solution for security and safety.
2nd Generation: Fully connected cameras, with upto two deployed in the vehicle – often with one looking out of the cab and one looking in the cab at the driver to monitor behaviour and look for warning signs such as drowsiness.
3rd Generation: Connected ADAS (Advanced Driver Assistance Systems) with upto eight cameras placed around and inside the vehicle to both help drivers and record events and incidents. This is the standard that programs like London’s Direct Vision Standard are fostering on the fleet management community.
Smartphone Apps
1st Generation: Apps that have to be activated by the user before they come online, and using the sensors (accelerometers, GPS) in the smartphone to gather data.
2nd Generation: Auto-activating apps that are linked to the vehicle’s internal systems and come online automatically when the vehicle is started up. Still using the internal sensors of the smartphone for data generation.
3rd Generation: Apps with Bluetooth Tags – a smartphone app that is working with sensors placed around the vehicle, communicating via Bluetooth. This turns the app into a sophisticated monitoring and reporting solution, that is connected via the phones data, and expands immensely on the data that the smartphone can gather internally, providing an alternative to the established Black Box solution.
Ancillary Sensors
1st Generation – No examples of these, corresponding to 1st generations of the other hardware items
2nd generation – wired sensors reporting back to the Black Box. Not directly connected themselves and reporting on things such as temperature levels in a refrigerated truck. These require a physical connection (wired) to the vehicles black box to transmit the data out of the vehicle
3rd generation – wireless sensors using a SIM to communicate directly, allowing for the deployment of a range of sensors that do not need to connect to the Black Box for transmission of data.
Within these generations, there is also a move away from the need for a dedicated Black Box solution, to more tailored and specific options for the fleet operator, through the use of 3rd Generation cameras, smartphone apps and ancillary sensors.
In essence as the technology has developed the flexibility and range of the solutions available to the operator has increased.
While this comes with the issue of more data from more sources, all of which needs to be compiled, monitored and analysed, it does give the options for very specific solutions to meet the security and safety needs of the operator.
The future
Beyond the 3rd Generations, the next technology jump will come with the deployment of 5G networks.
The logarithmic increase in speed and bandwidth that 5G will bring, changes the nature of the data flow both from and to the vehicle.
Vehicle to vehicle, and vehicle to infrastructure communications become possible, moving the ADAS and autonomous vehicle models forward.
More sensors can be placed on vehicles, and be connected over the network, reporting in real time. Giving operators an even greater range of solutions specific to their fleet management, security, and safety needs.
Step two: Collection.
The second step in the management process for using connected vehicle technology for better security and safety is the collection of key data sources.
While the connected vehicle is at the heart of the solution, other sources are just as key, in CMS’ experience, if the operator is to get a full 360-degree view of the risk profile.
As such we recommend incorporating employee, dispatch, and checkpoint/security information into the data mix, along with the established telematics and maintenance information.
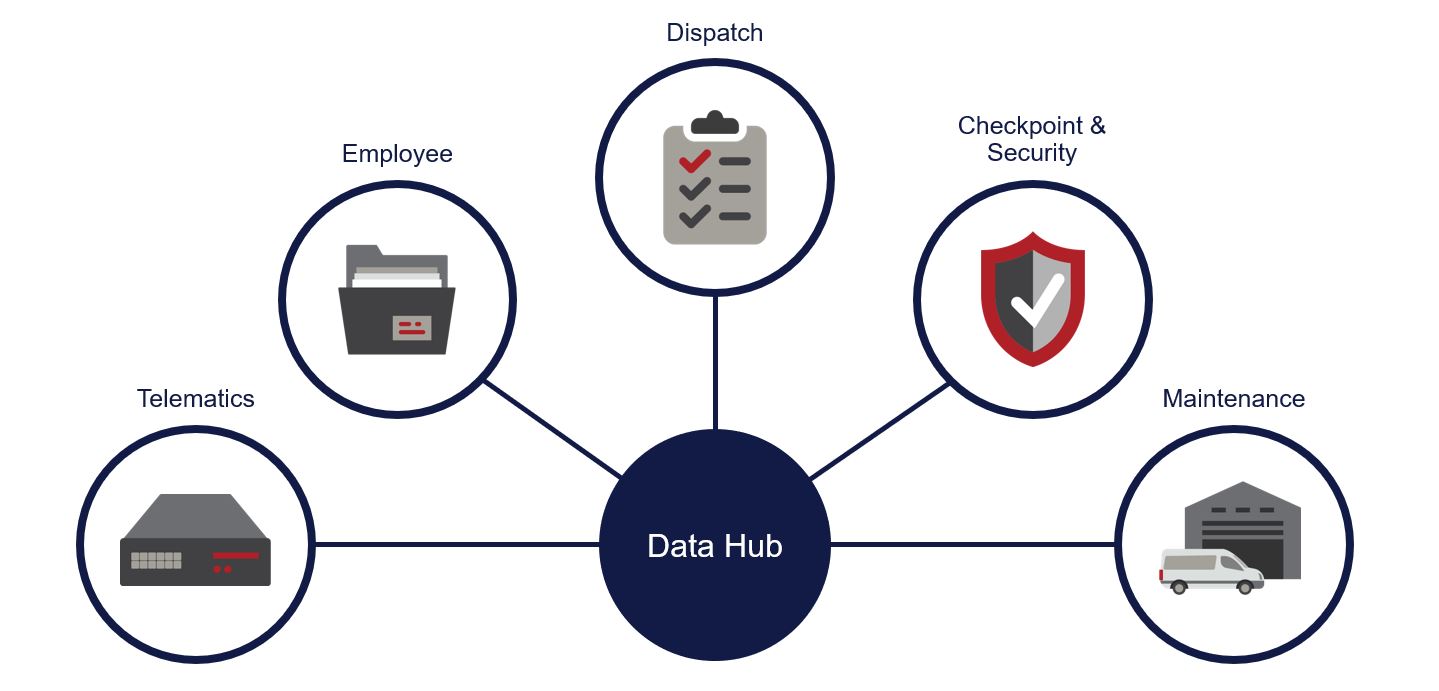
Of course, this is more data to add to the data lake, for processing, comparing, and analysing. But without incorporating the latest driver training records or performance review, the assessment of that driver’s risk-based security and safety is missing a major slice of the picture. Which could, at times, be the crucial element.
Step three: Analysis.
While the technology exists to gather all sorts of vehicle information, in real time. And most companies have good additional records on their employee’s performance, which can be incorporated into their fleet risk management program. All of this fails to have an impact if the wrong questions are asked of all this data.
CMS’ work in fleet risk management, has highlighted that simple questions are the foundation of what needs to be asked.
By asking these the areas of fleet security and safety which need action, can be identified, drilled down on and the actions that follow from the analysis be more effective.
Examples of these simple questions are
Who is high risk?
What behaviours are high risk?
Why are they high risk?
When are these risks occurring?
Where are these risks occurring?
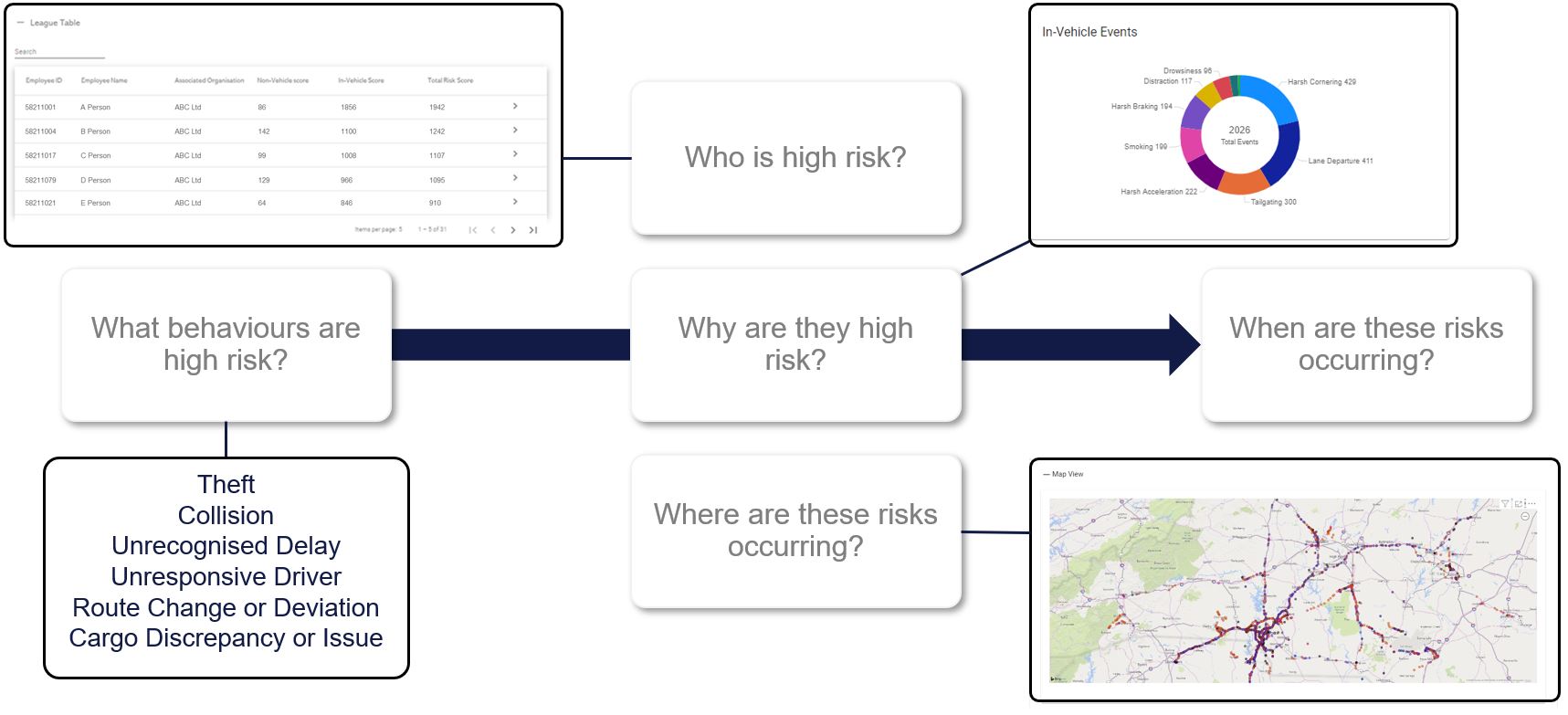
By focussing on these questions, large gains in security and safety can be made.
Step four: Action.
The final step in the management process for improving security and safety in the supply chain is, unsurprisingly, the most important one. Take action.
It is the step of effective monitoring and then acting on the data insights to keep people, vehicles, and cargo, safe and secure.
Again, based on CMS’ experience, the best way to do this is to have a dedicated team that is monitoring the data, responding to the insight, verifying the situation with the drivers, and then updating the management process with the outcome.
Of course, this vital step is built on the previous steps of connecting, collecting, and analysing the data. But without it, these steps are irrelevant.
Also, while the actions taken in this step are very much facilitated by the technology deployed, they are also a management task. As such the outcomes at this step are as much about the quality, training, management and leadership of the team, as they are about the technology supporting them.
Summary and conclusions
Connected vehicle technology, or telematics-based solutions, are a great facilitator in improving safety and security in the supply chain.
As the technology develops, its capabilities for tracking, measuring, assessing, and providing insight are growing. This will take a major leap forward with the coming implementation of 5G.
However, in CMS’ experience of fleet risk management, and working with connected vehicle technology, the management structure facilitated by the lakes of data and insight that the technology creates is as important, if not more so, than the technology itself.
Great technology with poor management will give a poor result. OK technology with great management will give a better result.
So, as much as we pride ourselves on what we can do with aggregating, standardising, and normalising connected vehicle and non-vehicle data. We’ve also learnt that the management processes behind fleet risk management are as vitally important if safety and security are to be improved.
The above CMS Insight is based on a presentation by our CEO, Charles Smith, at the Expoportuaria 2020 conference.



